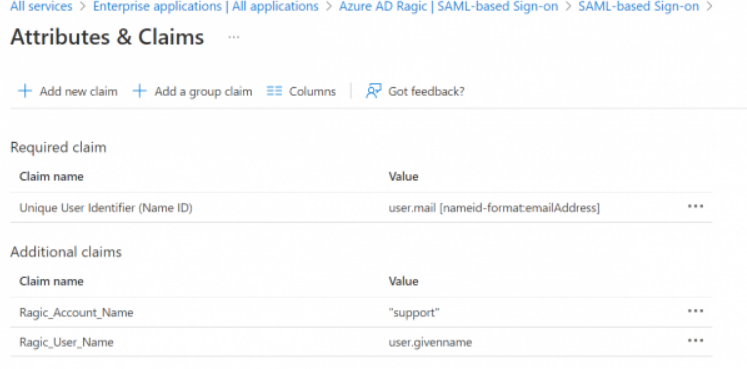
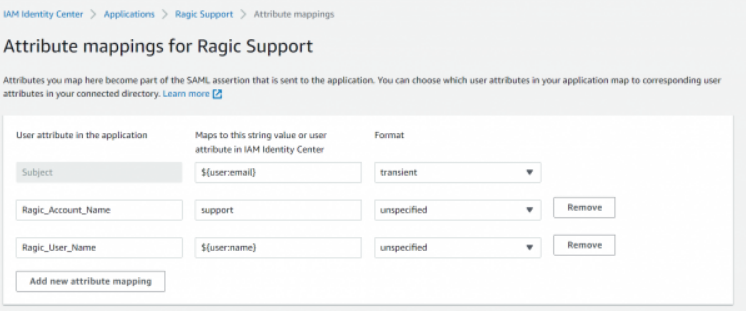
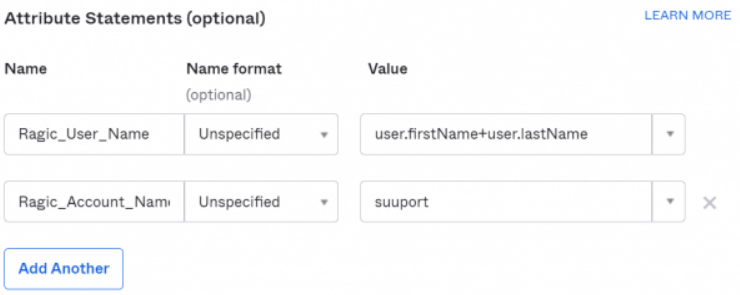
You can add a new attribute "Ragic_User_Name" in SAML Response. By doing so, if the login user account does not exist in Ragic, the system will automatically create a user account and its default email and user name will be the same as SSO's email. The password will be autogenerated as well. It's helpful if your plan is Concurrent Users.
If you want to let the identity provider (IdP) initiate SSO, you can add a new attribute in SAML Response:
Attribute Name: Ragic_Account_Name
Attribute Content: Account Name (If your database URL is https://www.ragic.com/support, then your account name would be "support")
You can refer to the setting process below:
Azure AD:
AWS:
OKTA:
If a user exists in multiple Ragic accounts (databases) and wishes to log in to Ragic through SAML SSO, the following conditions must be met:
1. Consistent Single Sign-On Configuration: In the company settings form of each Ragic account, the field values for "Identity Provider (IDP)," "Application Alliance Metadata URL," and "Application Identifier" must be consistent.
2. Allow SAML SSO Login: Users in each Ragic account must be able to log in through SAML SSO.
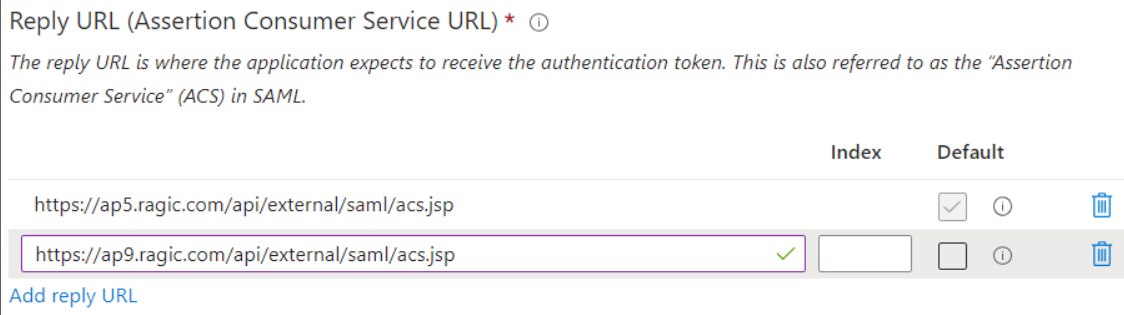
If the Ragic database accounts are on different servers, you need to ensure that the Identity Provider (IDP) allows configuring multiple Assertion Consumer Service (ACS) URLs. Currently, only Azure Active Directory (AAD) supports this feature.
Administrators need to find the Reply URL in the AAD application's SAML SSO settings and append "/api/external/saml/acs.jsp" to it for all user accounts belonging to different servers.
For example, if the Ragic accounts are located at "https://ap5.ragic.com" and "https://ap9.ragic.com," please add "https://ap5.ragic.com/api/external/saml/acs.jsp" and "https://ap9.ragic.com/api/external/saml/acs.jsp" to the Reply URL.